How adaptive MFA works
Rules evaluate contextual information about each action to determine the appropriate response:Common adaptive MFA scenarios
New device detection
Challenge users only when they’re signing in from an unrecognized device: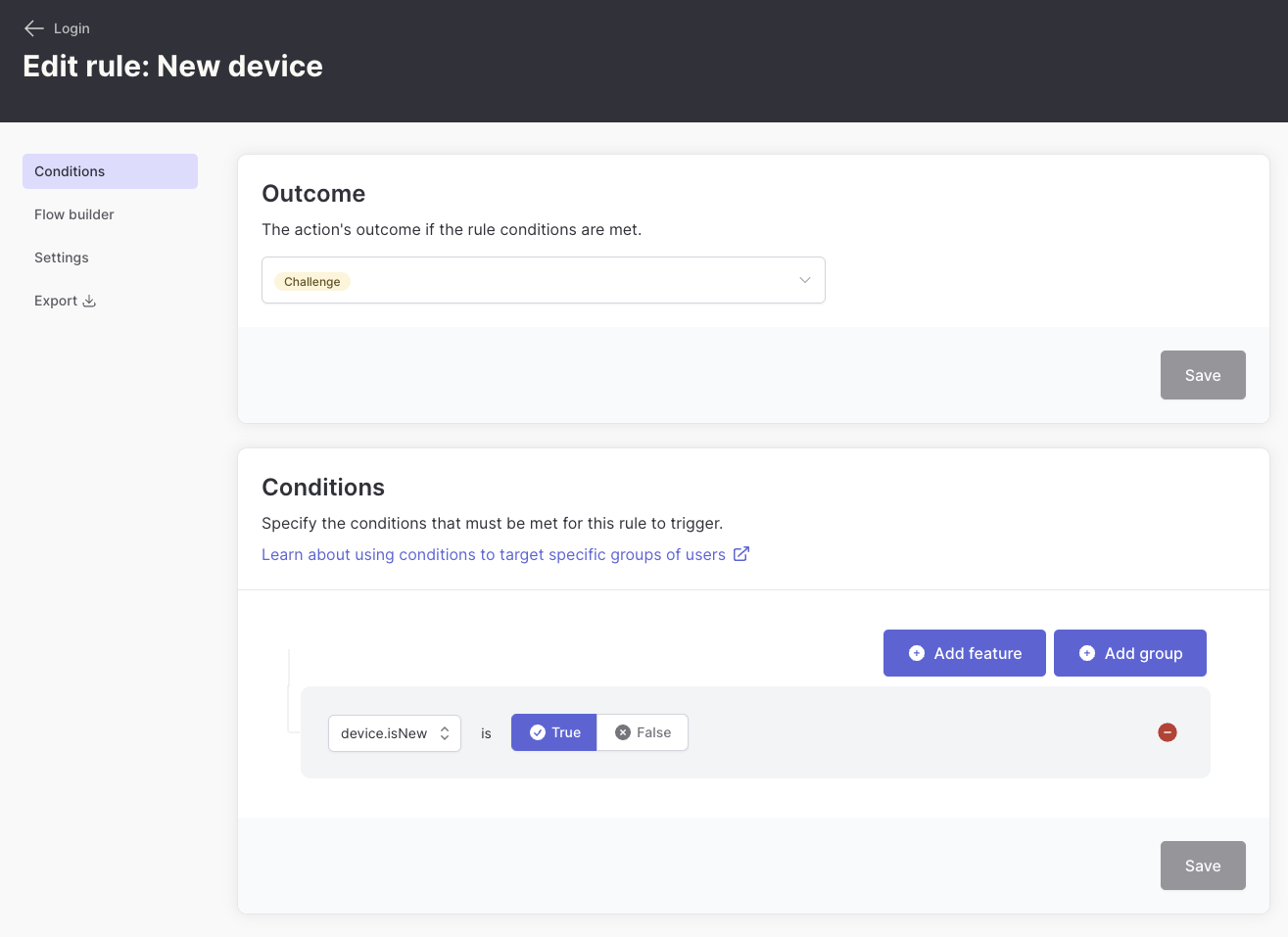
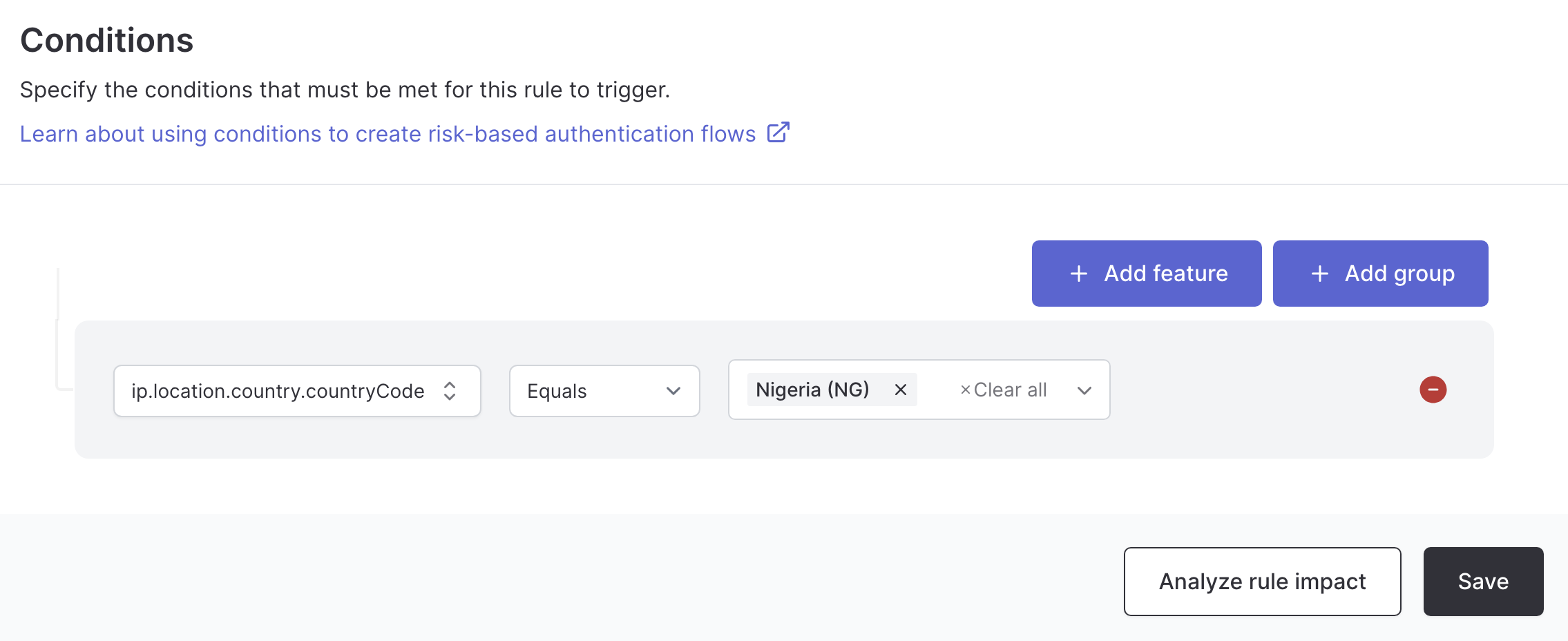
Location-based policies
Apply different authentication requirements based on user location:- Known locations: Allow without challenge
- New countries: Require MFA
- High-risk regions: Block or require strong authentication
Risk-based authentication
Create rules that consider multiple risk factors:- User behavior: Login patterns, time of day, frequency
- Device characteristics: Known vs unknown devices, device type
- Network information: IP reputation, VPN detection
- Transaction context: Amount, recipient, frequency
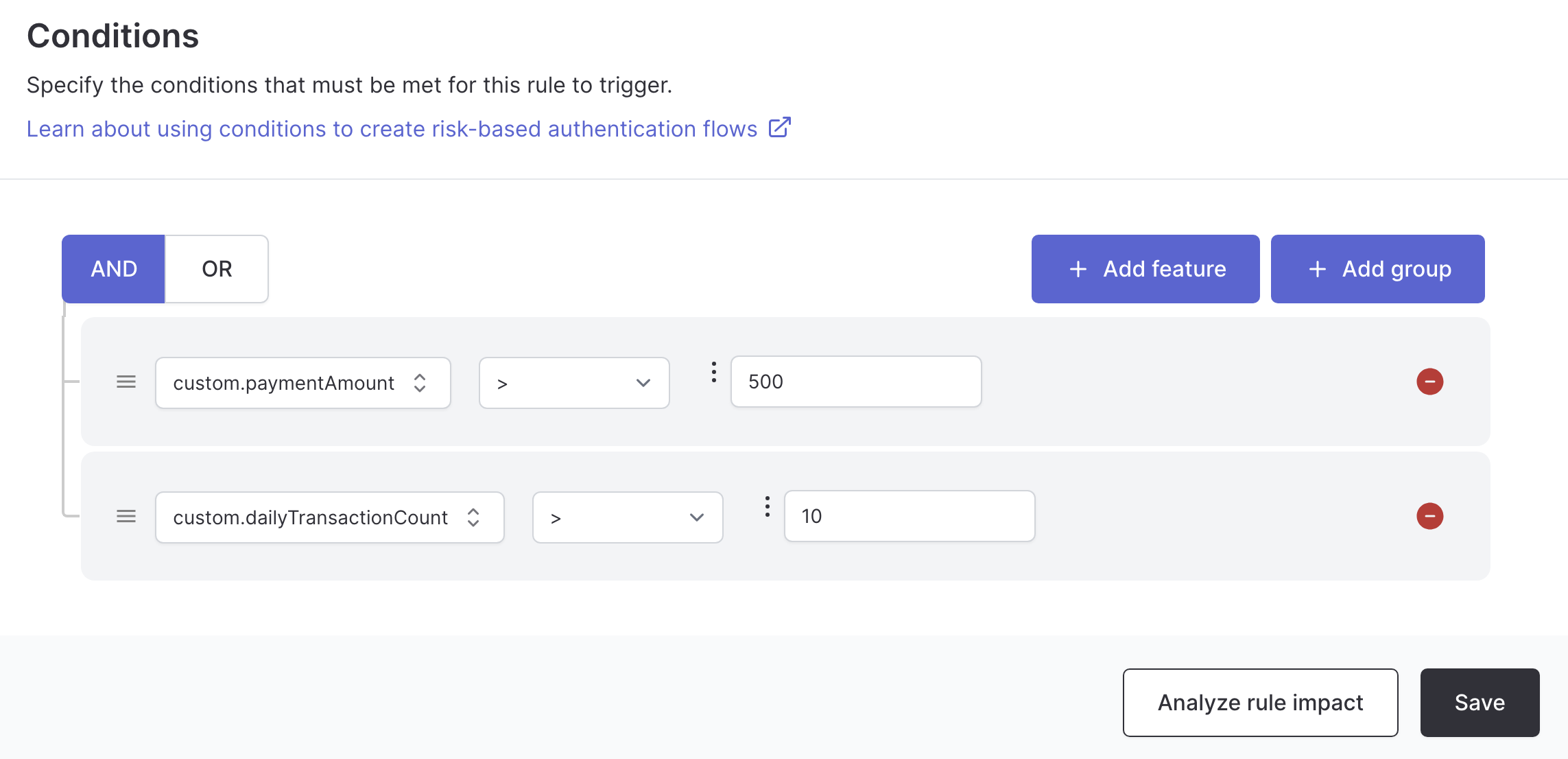
Business-specific adaptive MFA
You can create rules based on your application’s specific data points. For example, challenge users only for high-value transactions: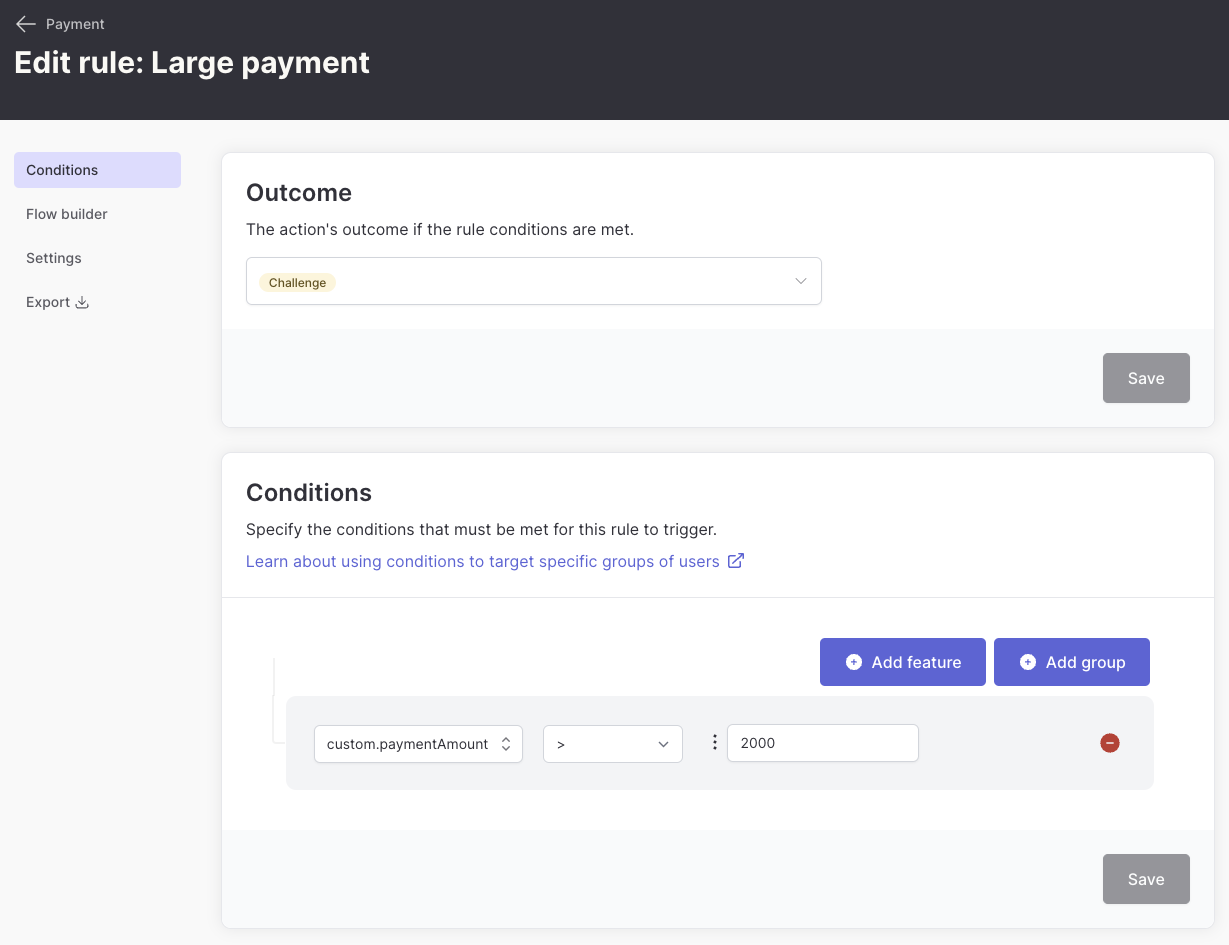
Rule examples
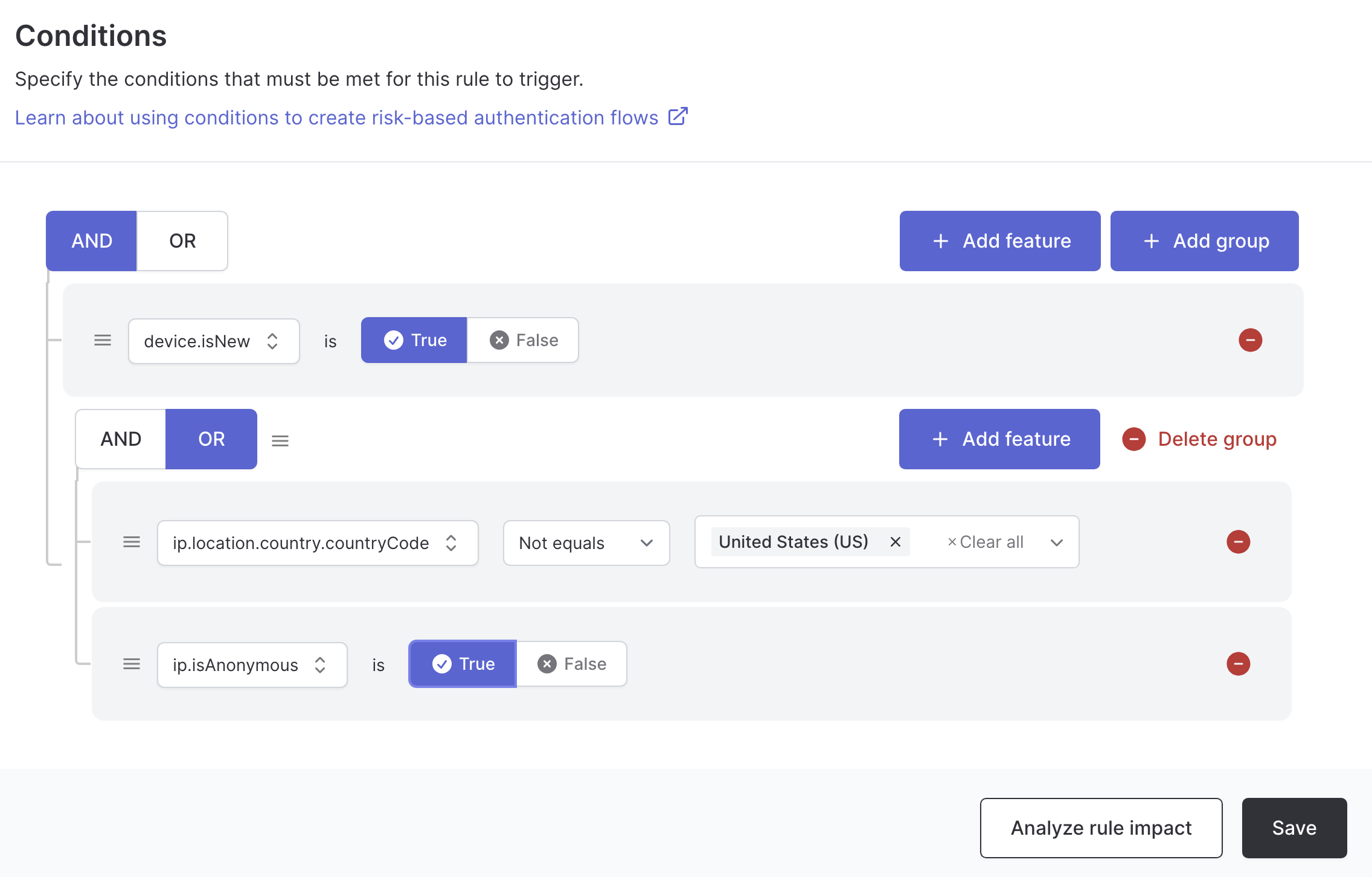
Device and location combination
Transaction pattern analysis using custom data points