Controlling the frequency of MFA challenges based on device
By default a user will be required to complete an MFA challenge every time they sign in. This behavior can be fine-tuned by configuring a rule for your Auth0 login action - for example, you could let users skip MFA if you know they have previously authenticated within the last 24 hours on the same device.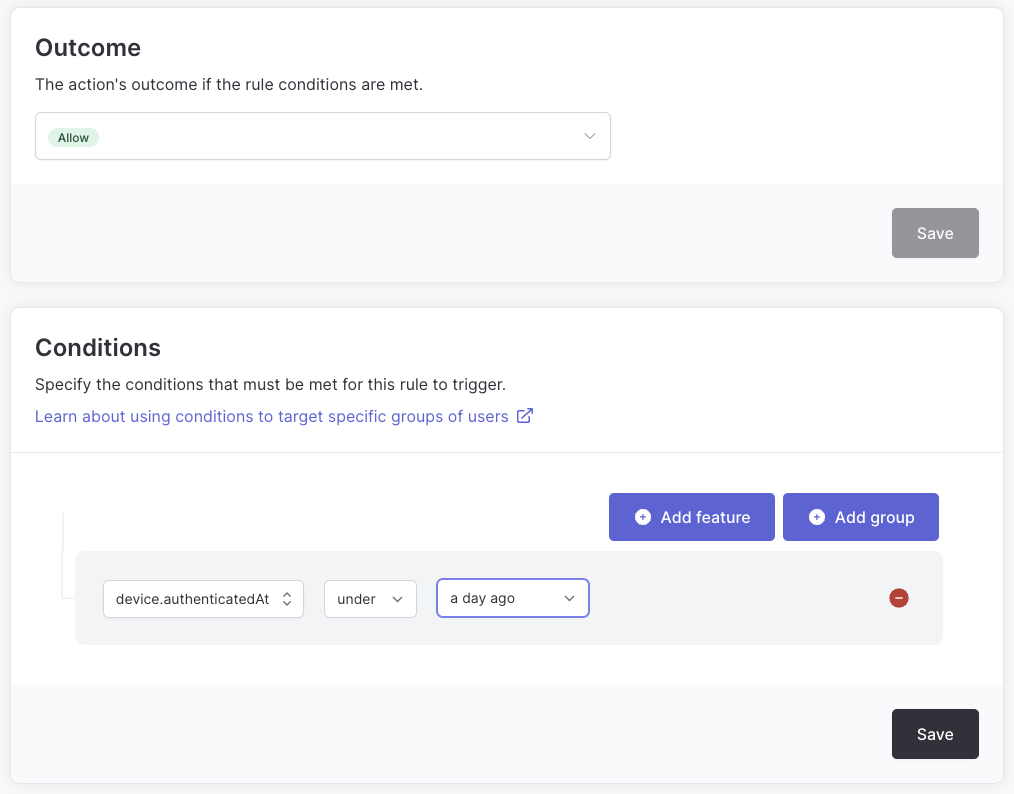
device_id as an authorization param in your Auth0 integration code.
If you are already tracking device ID in your own app you can pass this value - or use the Authsignal Web SDK to pass a persistent device ID which is stored in a cookie.
For example if using the auth0-spa-js library:
Opting out for social or federated logins
You may want to let users opt out of MFA if they are using an external social login provider, for example Google or Facebook. This can easily be achieved by checking the connection on theevent object.

