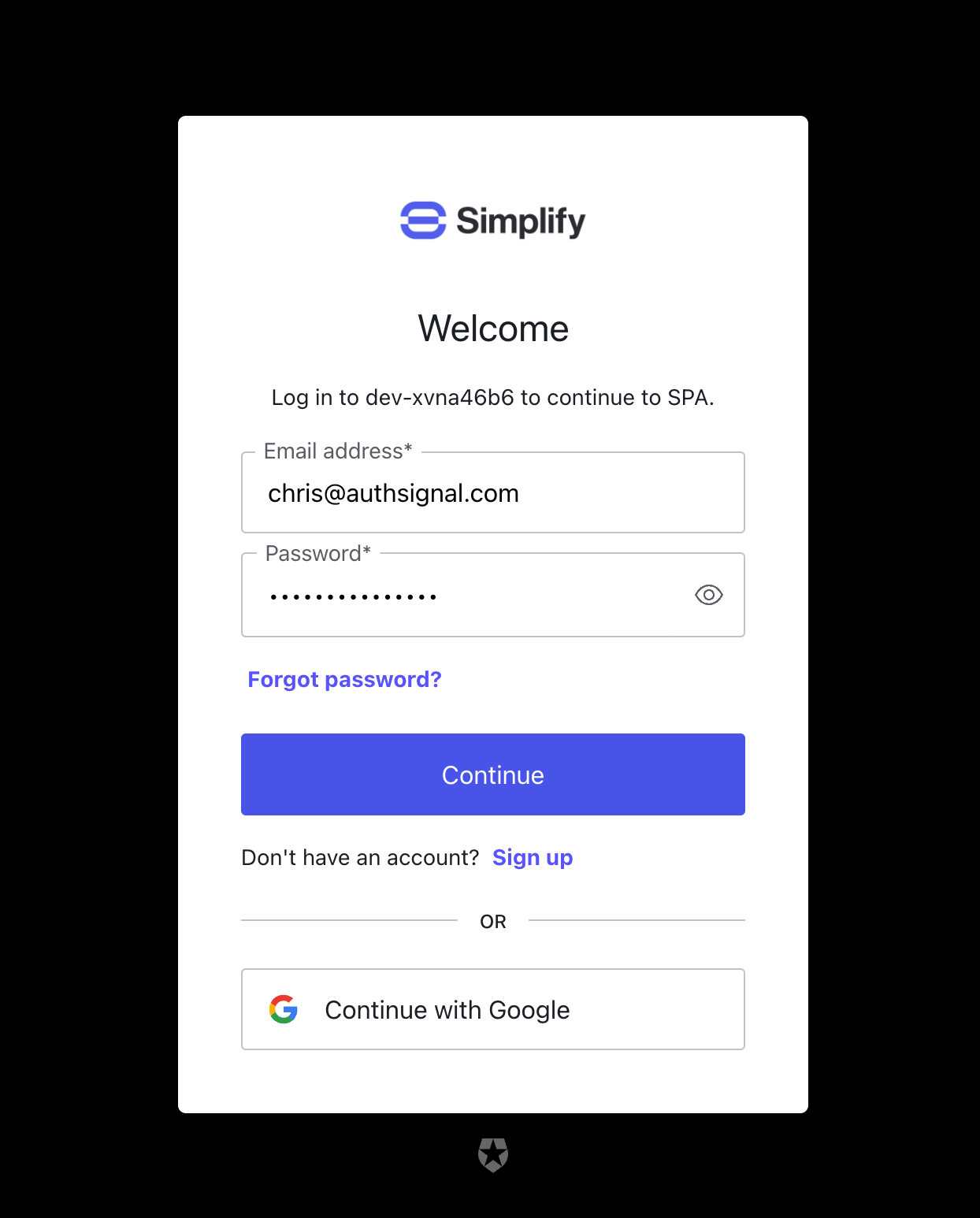
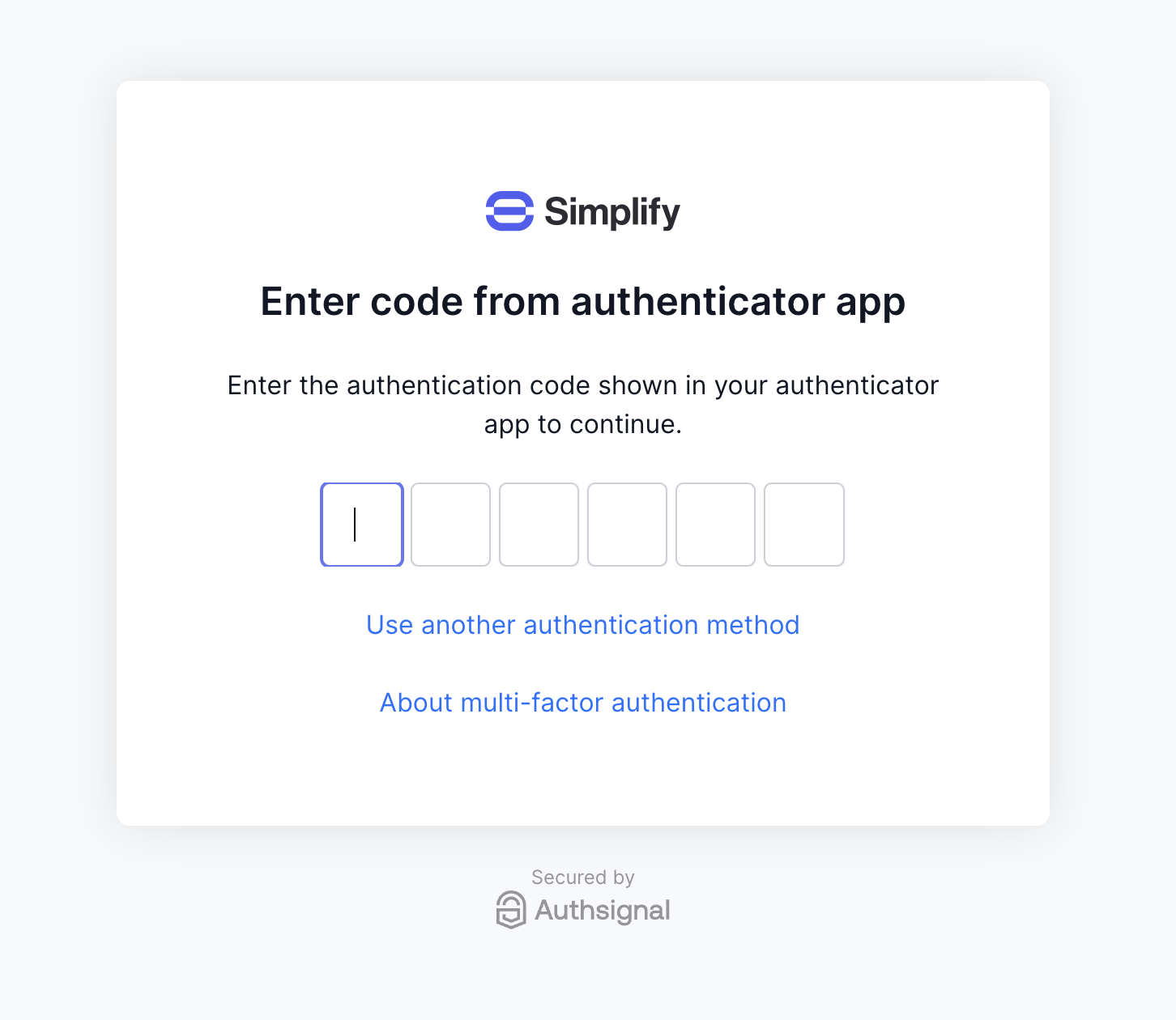
User flow
Integration steps
Create an action
In the Auth0 Dashboard, go to Actions → Library and select “Build Custom”. Then select the “Login / Post Login” trigger and give the action an appropriate name (for example “post-login-mfa”).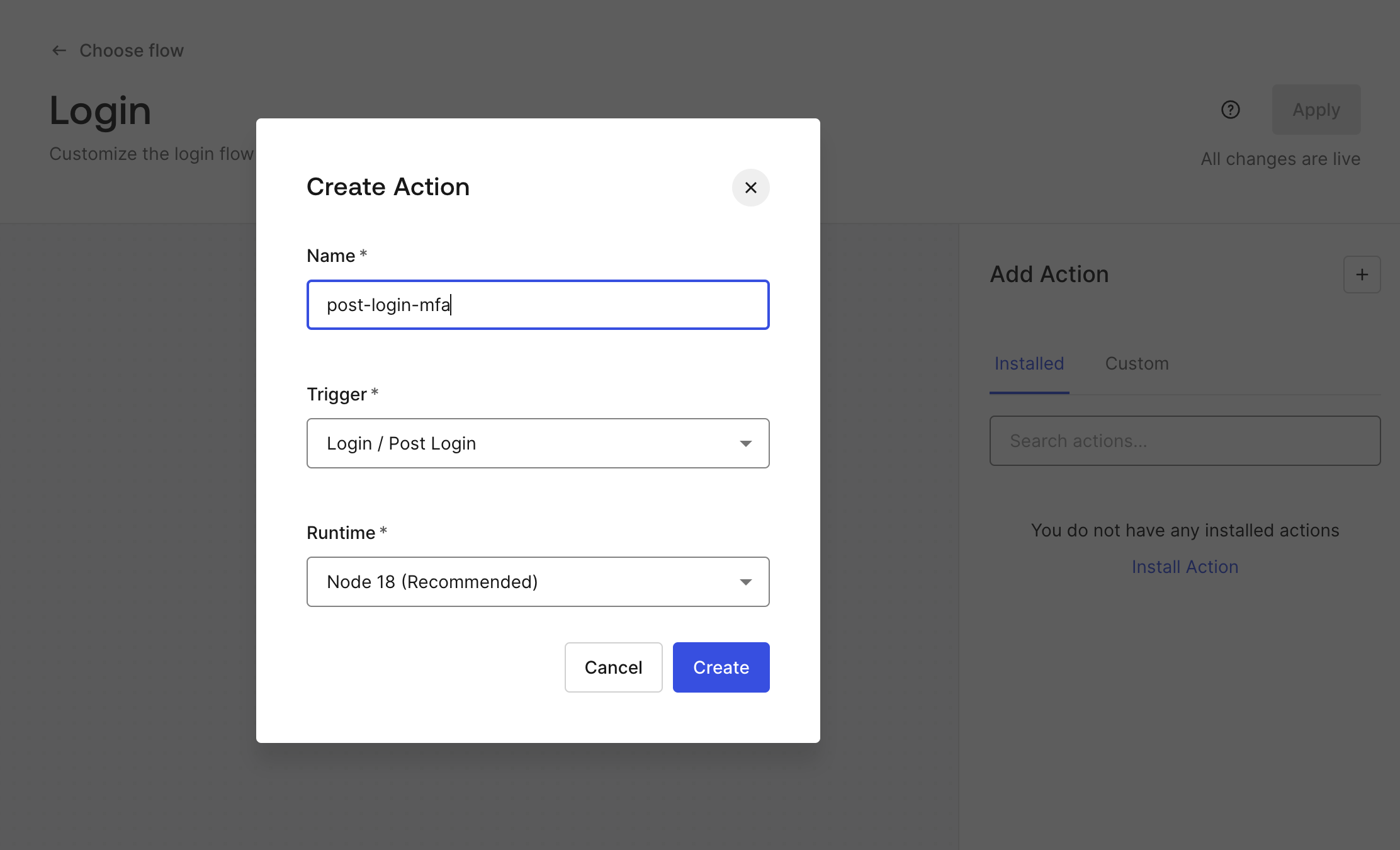

Add your secret
Now your action has been created, create a new secret called 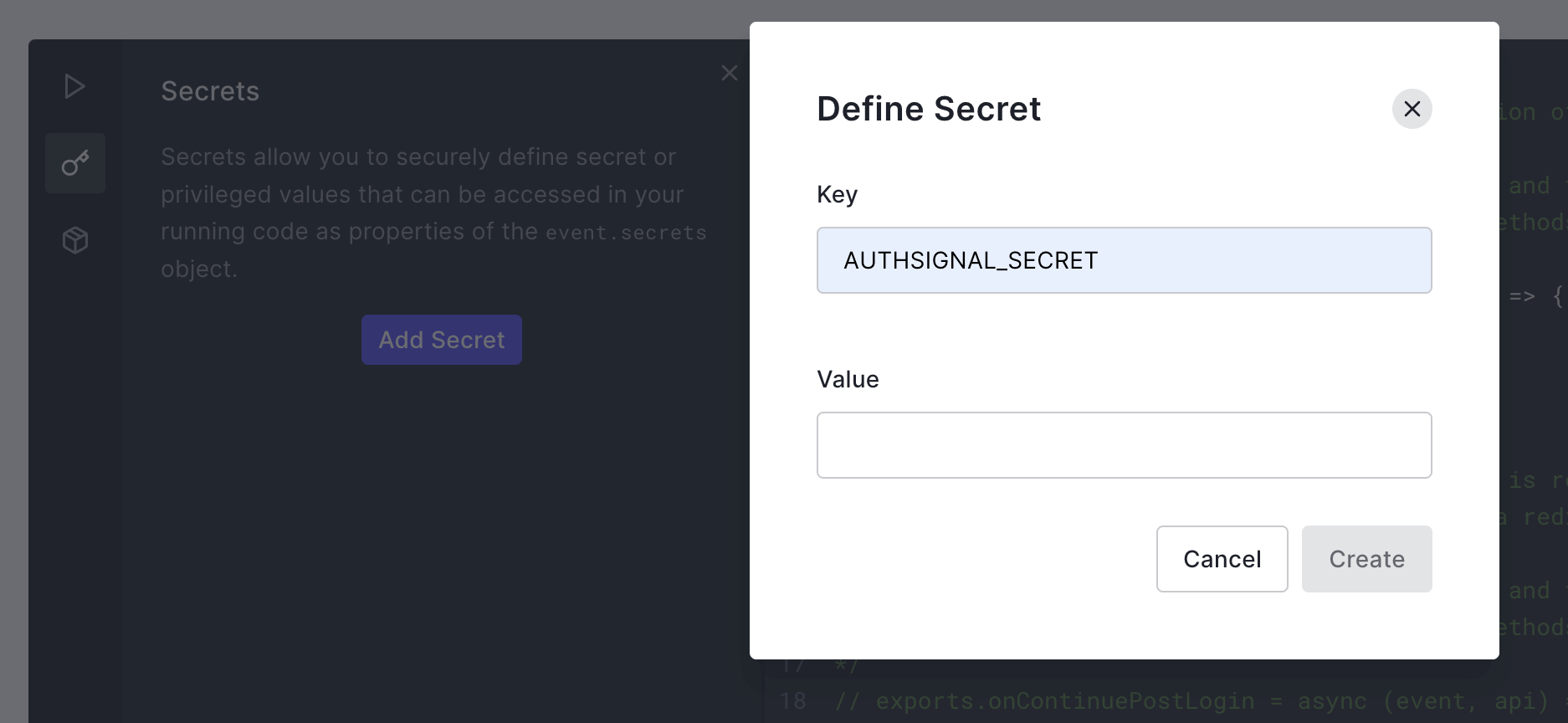
AUTHSIGNAL_SECRET and provide the value of your secret from the Api Keys section in the Authsignal Portal.
Add the action code
Add the following code snippet to the action.If using a non-US region (e.g. AU or EU) you will need to override the API URL as follows:
Connect your action to the Login flow
Now connect your action in the Flows section of the Auth0 Dashboard by dragging it into the Login flow.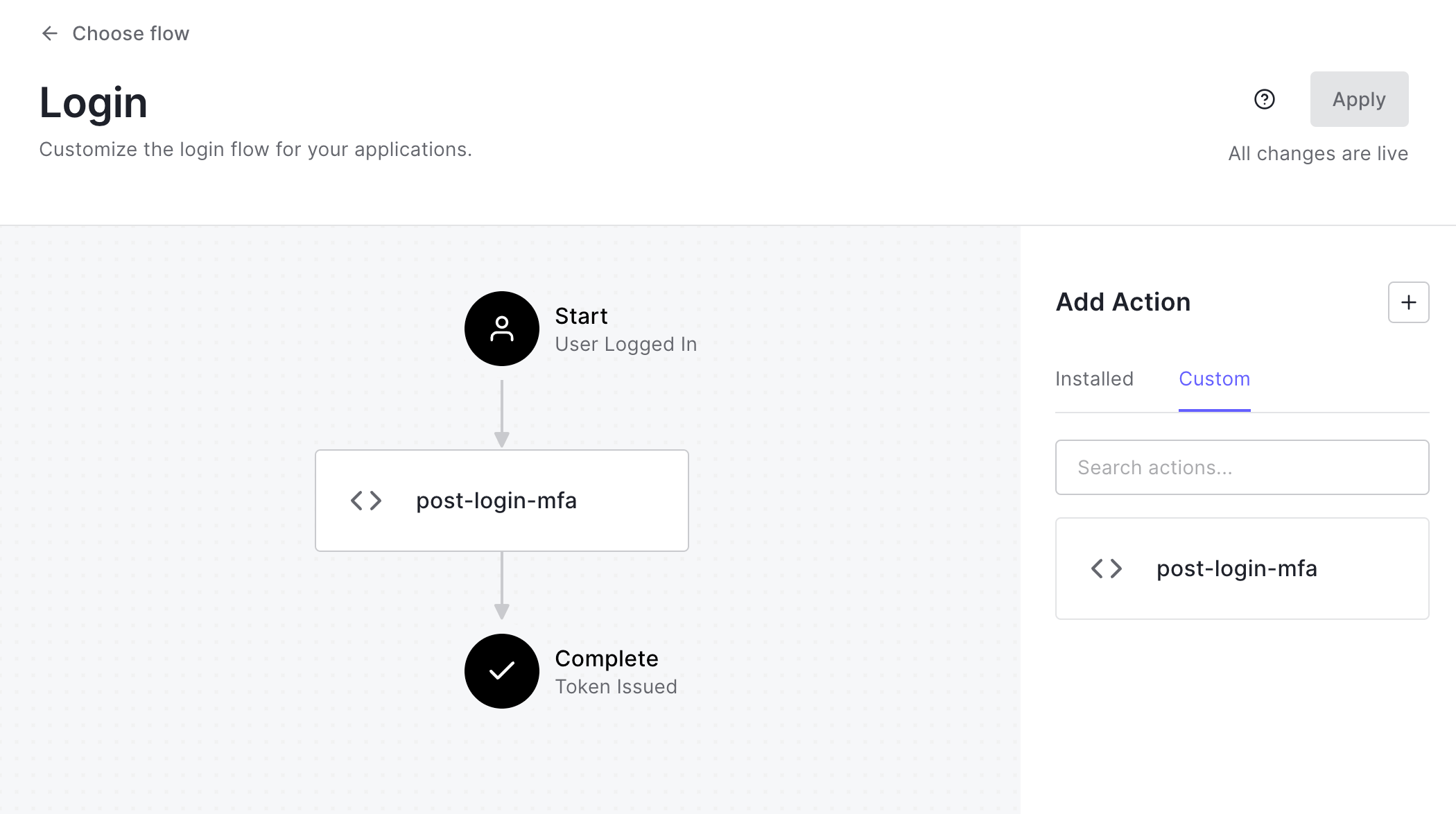

Configure the action in Authsignal
Once the previous steps have been completed, the next time the Auth0 action is run you will see an action appear in the Authsignal Portal called “Auth0 Login”. You will need to set the default outcome for this action to 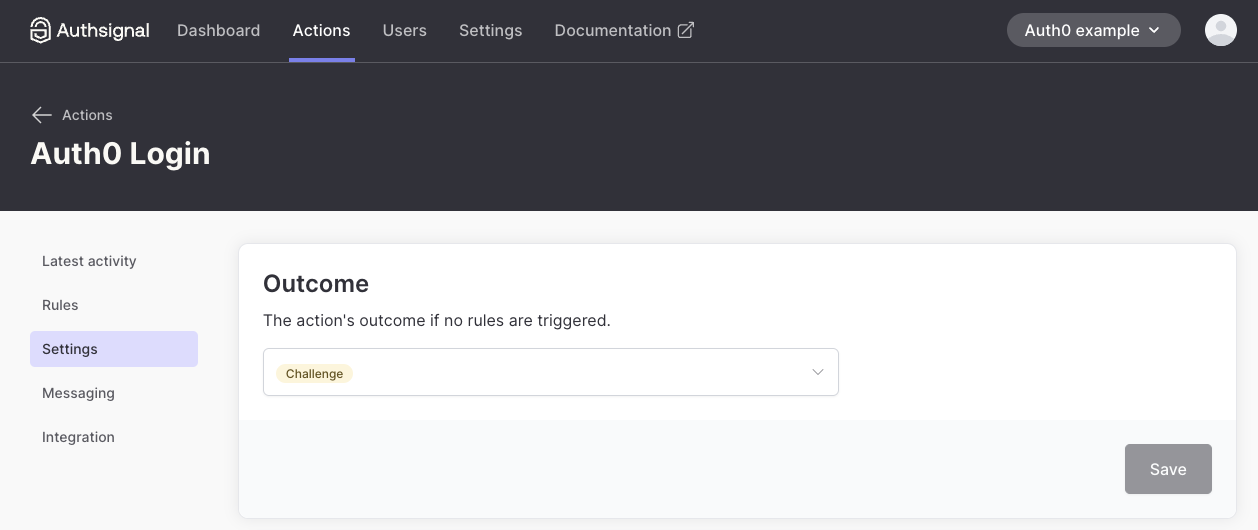
Challenge and save it.