Overview
In this guide, we will demonstrate how to leverage a Keycloak provider to seamlessly integrate MFA into a traditional username and password login flow using Authsignal’s pre-built UI, enhancing security with minimal disruption to the user experience.Keycloak provider code example
The above example can be extended to meet your specific requirements.
Prerequisites
This guide assumes you have a basic understanding of Keycloak and Authsignal. If you are new to Keycloak, we recommend you follow the Keycloak Quickstart guide to get up and running.Authsignal configuration
Enable authenticators
Head to the Authenticators section in the Authsignal Portal to configure authenticators.For this example, we have enabled Authenticator App.
Get API keys
Head to the API Keys section in the Authsignal Portal to get your API keys.
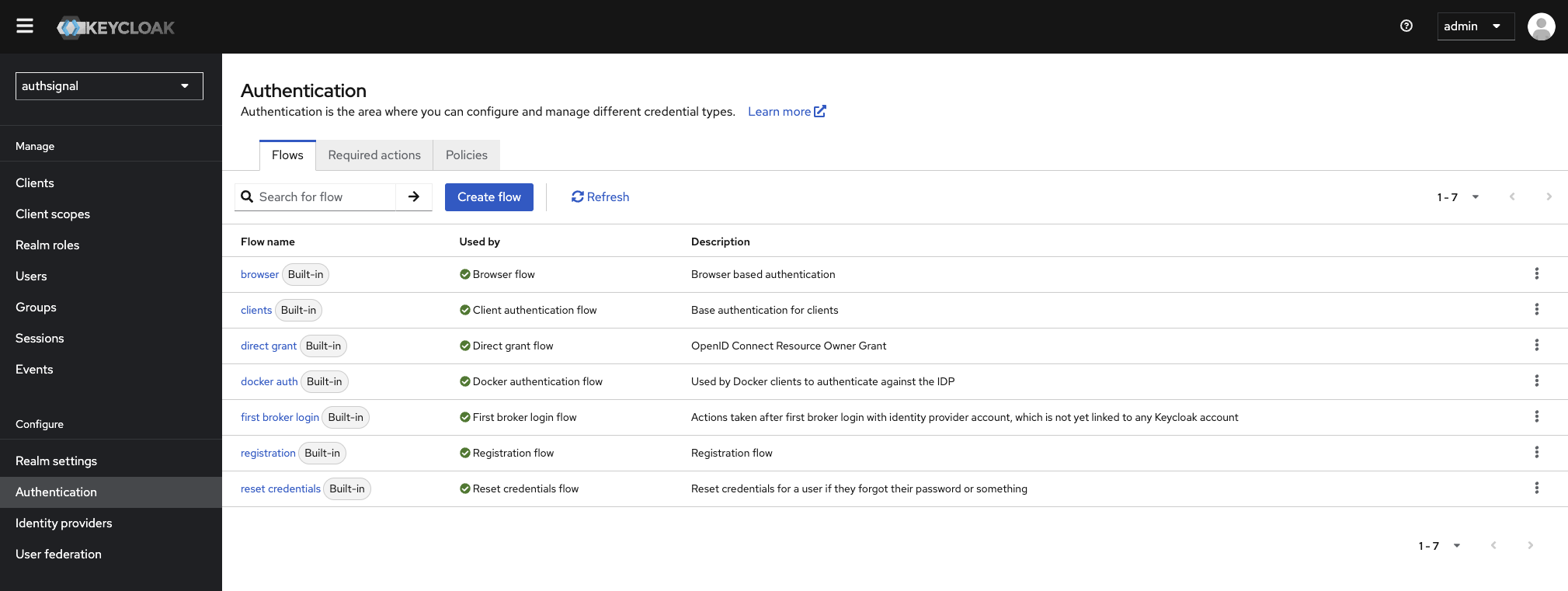
Keycloak configuration
Creating a new provider
Download the provider JAR files
Download the pre-built
authsignal-keycloak-*.jar
JAR file. Alternatively, you can build the JAR file yourself using the GitHub
repository.
Download the Authsignal Java SDK JAR file
Download the Authsignal (version 2.0+) Java SDK (dependency) JAR
file from Maven.
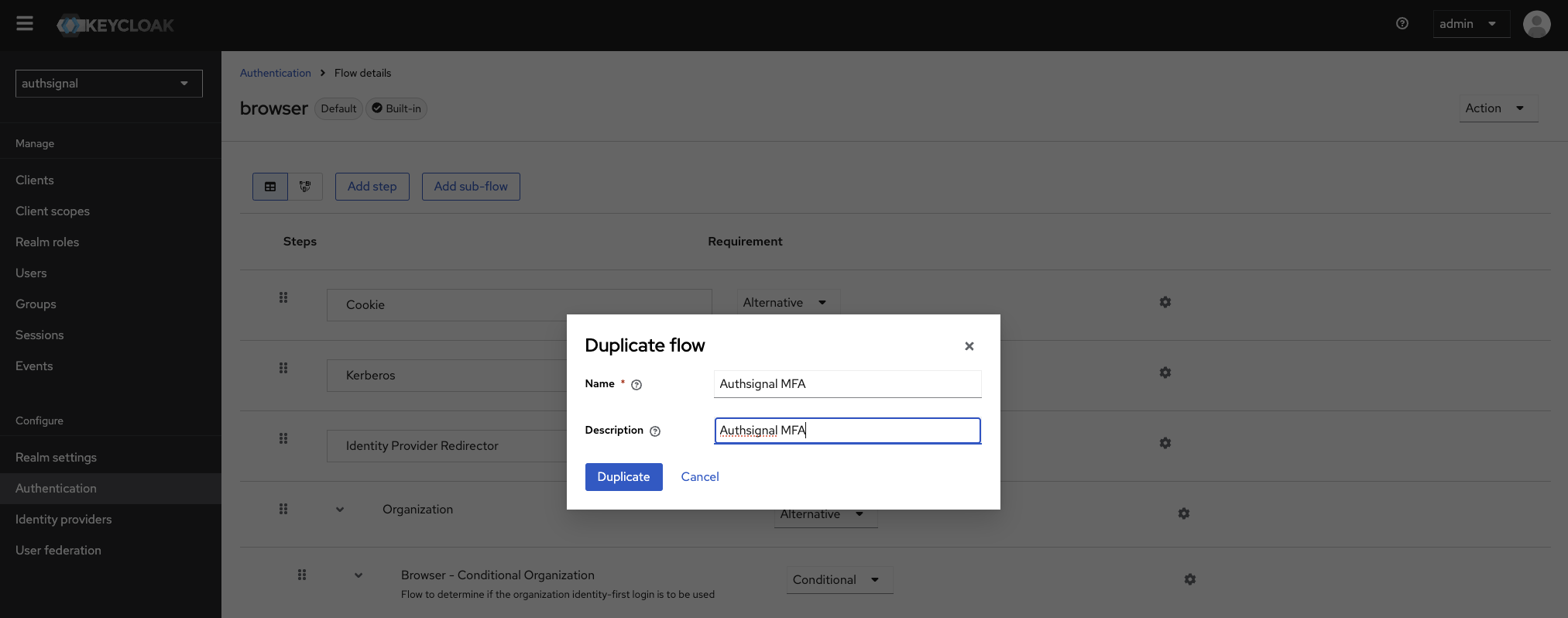
Configuring the Authsignal Authentication flow
If you have not already created a Keycloak realm, do this by clicking the Create realm button
in the Keycloak admin UI (within the Keycloak drop-down menu top left).
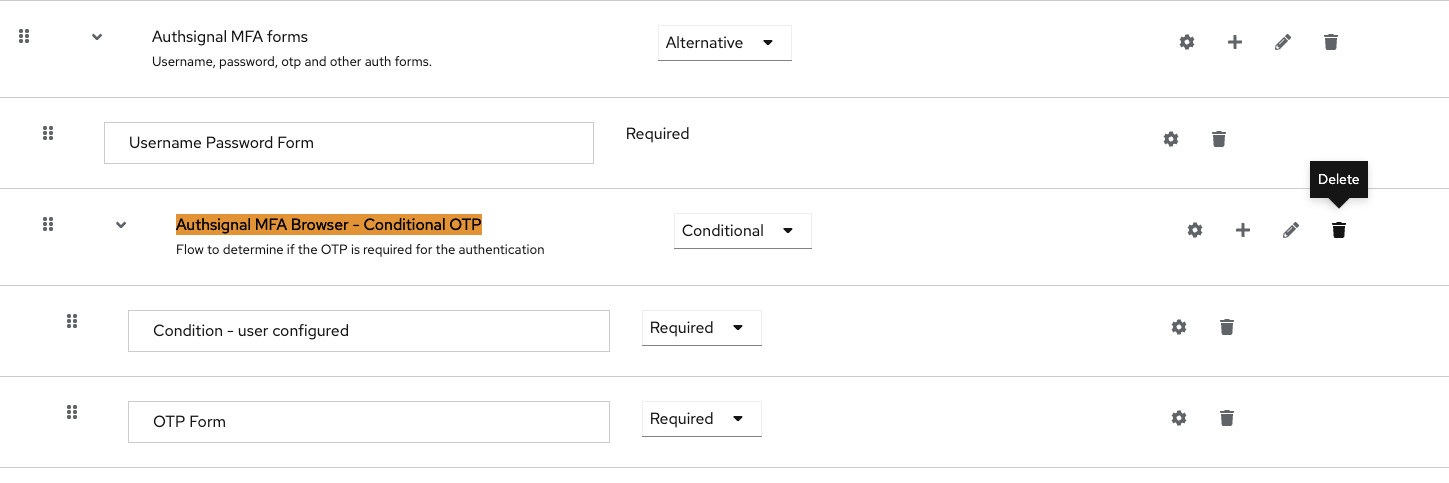
Add the Authsignal provider to the flow.
Inside the subflow which already contains the ‘Username Password Form’, we need to add the Authsignal provider as a step.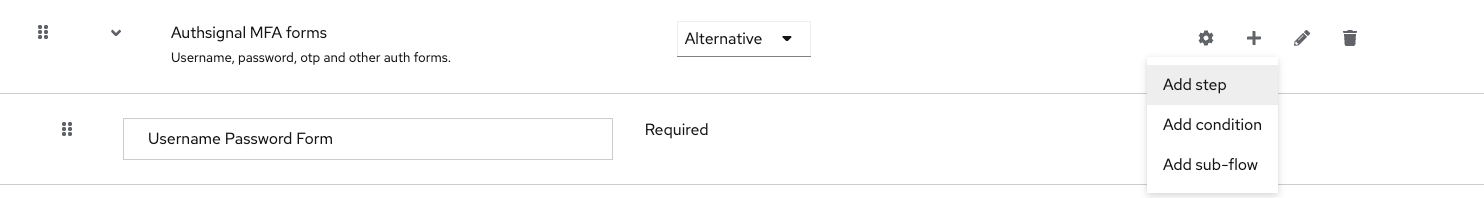

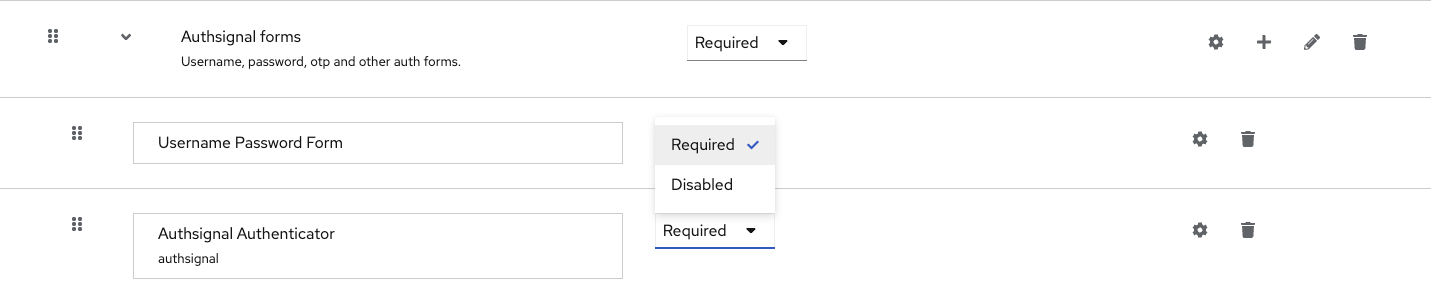
Select the Authsignal Authenticator.
If you successfully added the Authsignal .JAR files to the 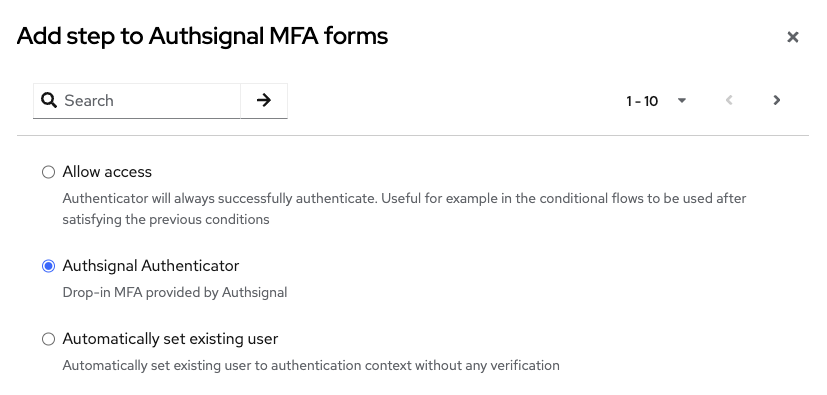
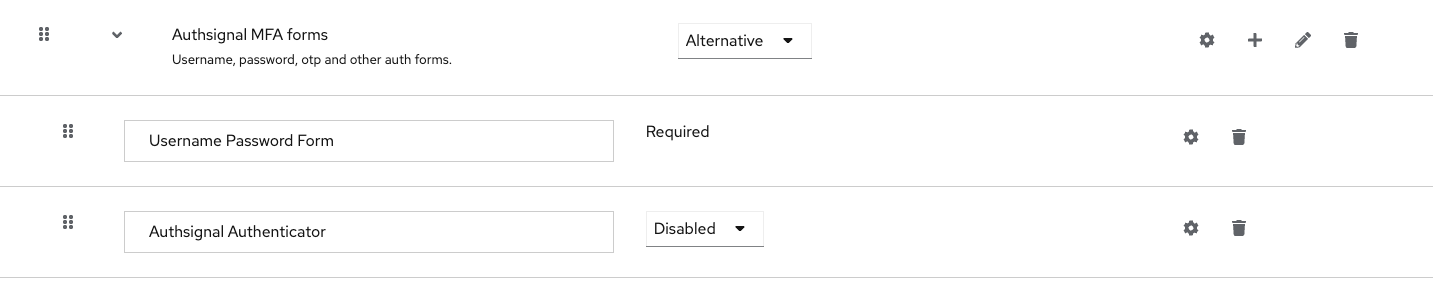
/providers/ folder in the previous steps, you will see the Authsignal Authenticator listed in the menu - select it to add it to your flow.

Click the settings cog on the Authsignal Authenticator step.
Add your Server API secret key and API host.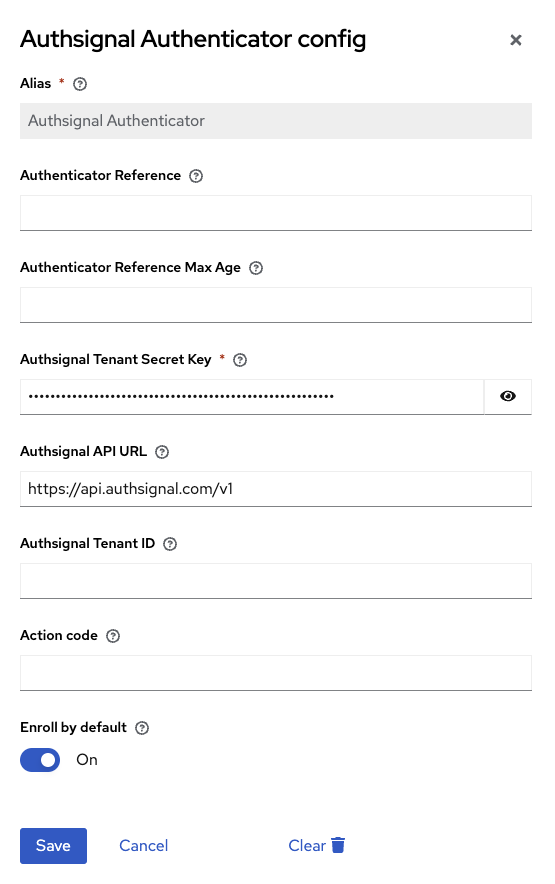

Conclusion
That’s it! You’ve successfully added MFA to your Keycloak login flow using Authsignal. To test the flow, log in and you will be prompted to enroll an authenticator. The next time you log in, you will be prompted to complete an MFA challenge.Want to use Keycloak groups and roles in your authentication rules? See the Groups and Roles
guide for instructions on setting this up.