- Custom UI - Build your own UI using our Client SDKs for web and mobile when you need complete control over the user experience.
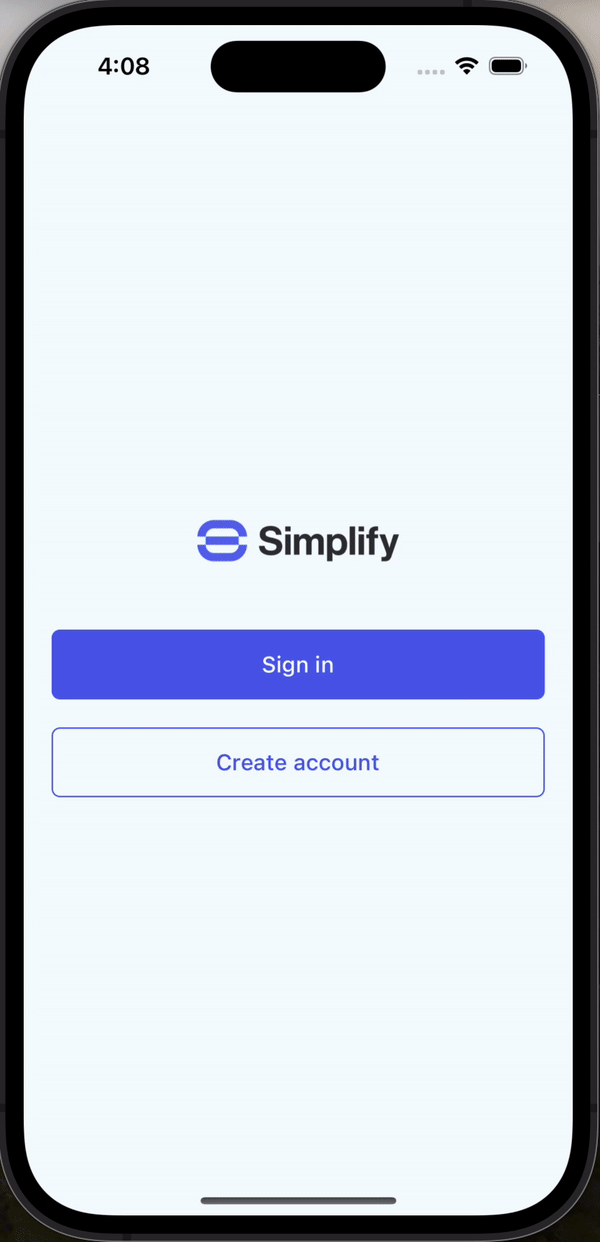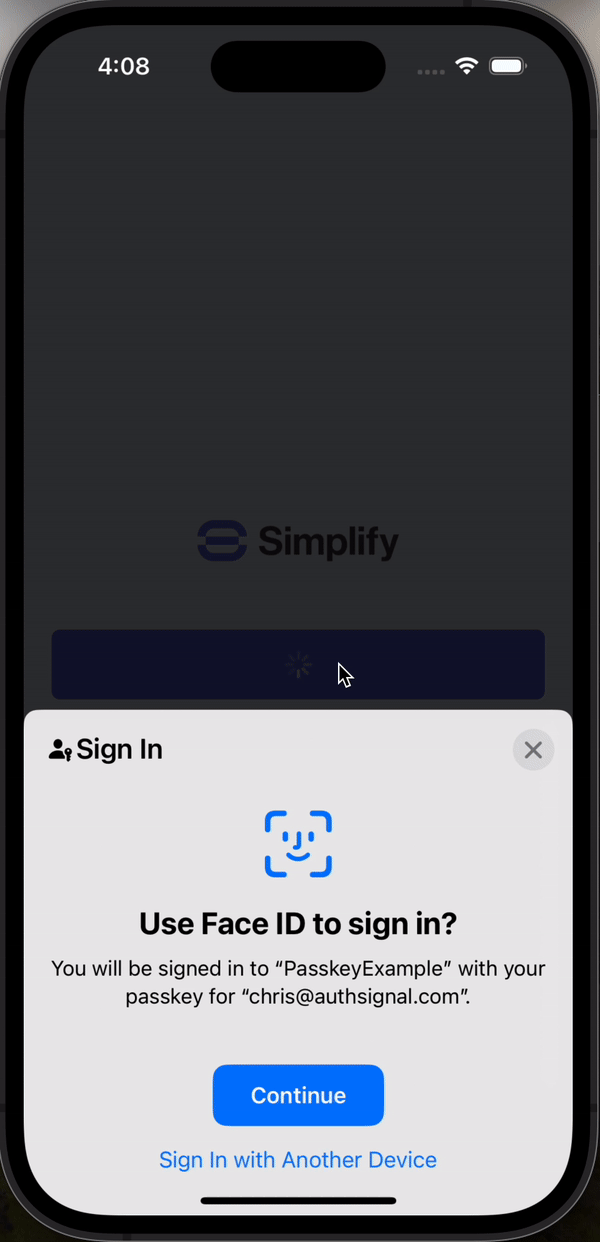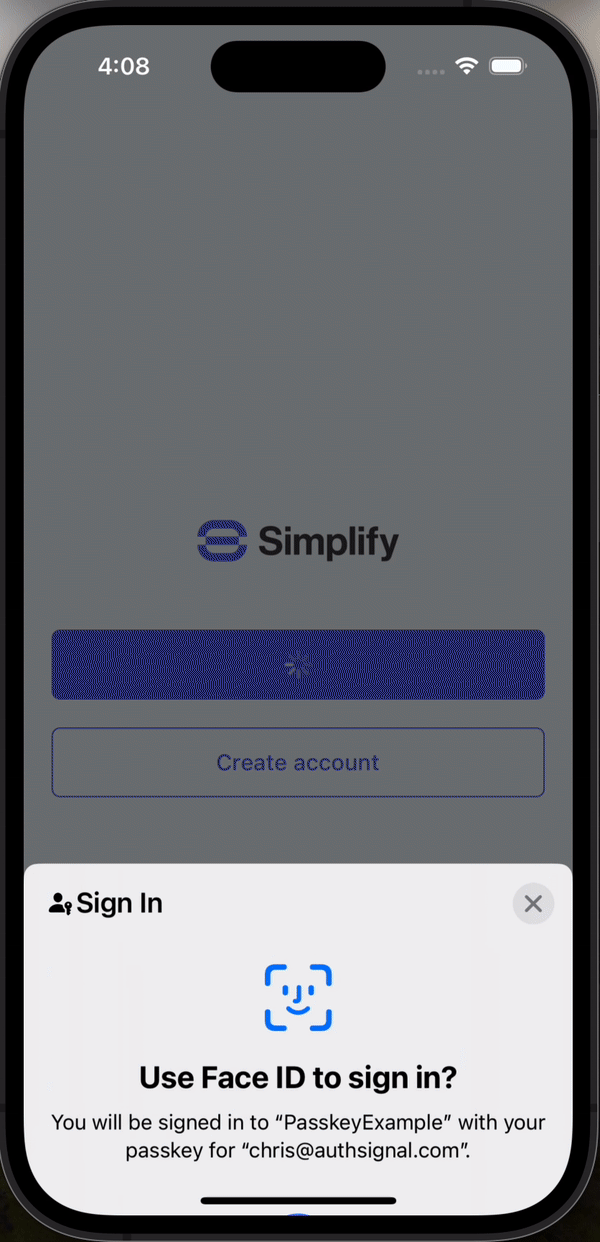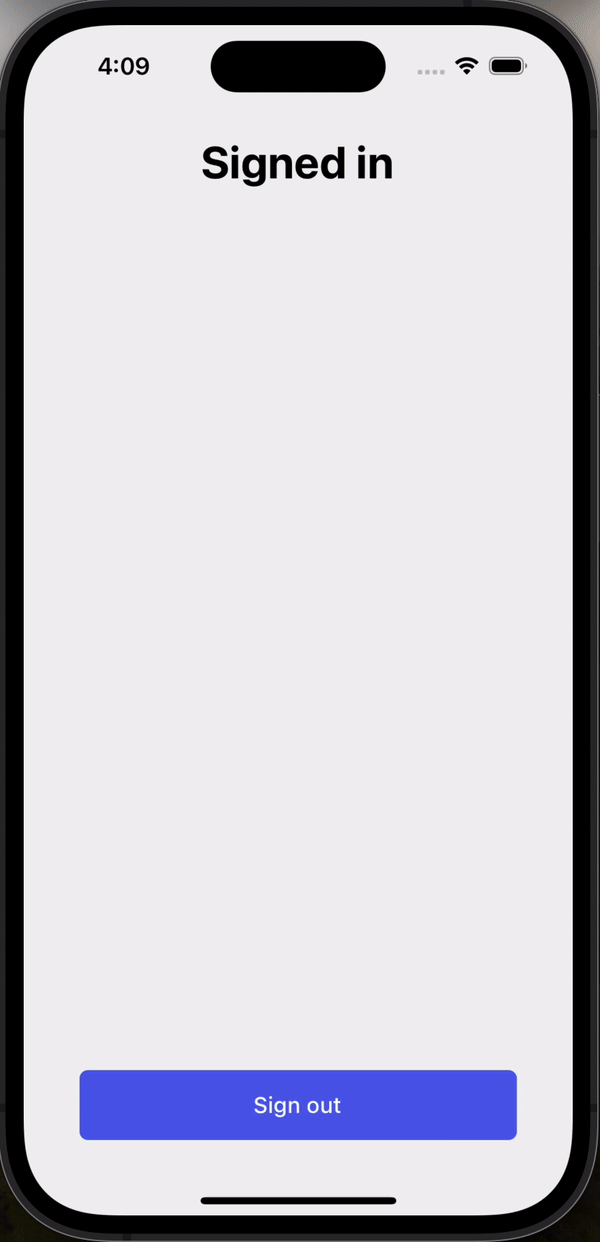
- Pre-built UI - Drop in our ready-to-use hosted UI that supports passkeys, SMS and WhatsApp OTP, and more. You can customize the design to match your brand.
Github example code
Lambda integration steps
1. Create auth challenge
The first lambda trigger which we will use is Create auth challenge.- Custom UI
- Pre-built UI
We will use the Authsignal Server SDK in this lambda to return a short-lived challenge token.We’ll also return whether the user is enrolled or not, so we know which Client SDK method to use in a subsequent step.
2. Verify auth challenge response
The second lambda trigger which we will use is Verify auth challenge response.- Custom UI
- Pre-built UI
In this lambda we will take the validation token obtained from the Authsignal Client SDK and pass it to the Authsignal Server SDK to verify the challenge.
App integration steps
1. Obtain a username
Once the user has inputted their email address or phone number you can either:- Use this value as the Cognito username, or
- Use this value to find the user record in your database and obtain their username
2. Call SignUp (if required)
You can call SignUp either as part of a separate account registration flow, or “just-in-time” before every sign-in attempt (ignoring if the user already exists).3. Call InitiateAuth
The next step in authenticating with Cognito from your web or mobile app is to call InitiateAuth. This will invoke the Create auth challenge lambda which we have implemented above to return an Authsignal challenge token.- Custom UI
- Pre-built UI
Here we obtain a challenge token to pass to an Authsignal Client SDK.
4. Use Authsignal
The next step is to use Authsignal to handle presenting the user with a challenge.- Custom UI
- Pre-built UI
Use an Authsignal Client SDK to present the user with a challenge.Here we show email OTP but our SDKs support a variety of methods including SMS or WhatsApp OTP, email magic link, authenticator app, and more.
5. Call RespondToAuthChallenge
The final step of your app integration is to call RespondToAuthChallenge. This will invoke the Verify auth challenge response lambda which we have implemented above to complete authentication using our Authsignal validation token.- Custom UI
- Pre-built UI
Pass the validation token obtained from the Authsignal Client SDK to Cognito as the challenge answer.

