What is authenticator binding?
Authenticator binding is a security principle that ensures users can only add new authentication methods after proving their identity with existing methods. This prevents attackers from adding their own authenticators if they compromise a single factor.Once a user has MFA enabled, adding new authenticators should require authentication with an existing method. This prevents MFA bypass attacks.
Why binding matters
Consider this attack scenario:- Attacker compromises a user’s password
- Without binding: Attacker adds their own phone number for SMS
- Attacker now controls the “second factor” and bypasses MFA
How Authsignal handles binding
Authsignal provides different approaches depending on your implementation:Pre-built UI
Automatic binding with configurable options
Client SDKs
Flexible binding with full control
Using the pre-built UI
Automatic binding (recommended)
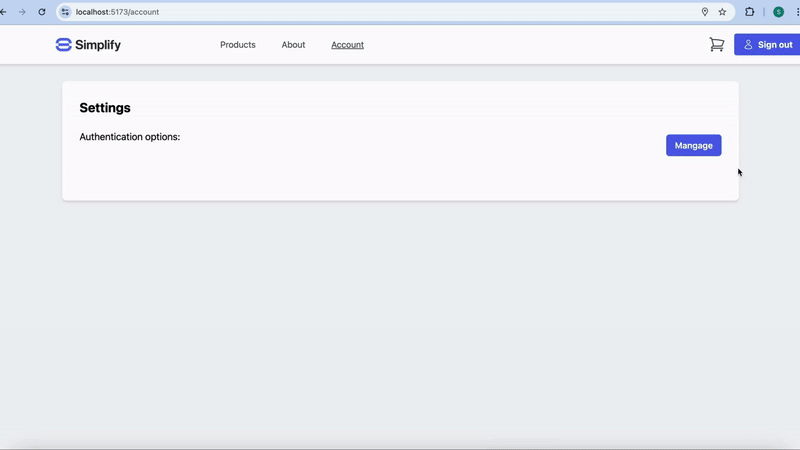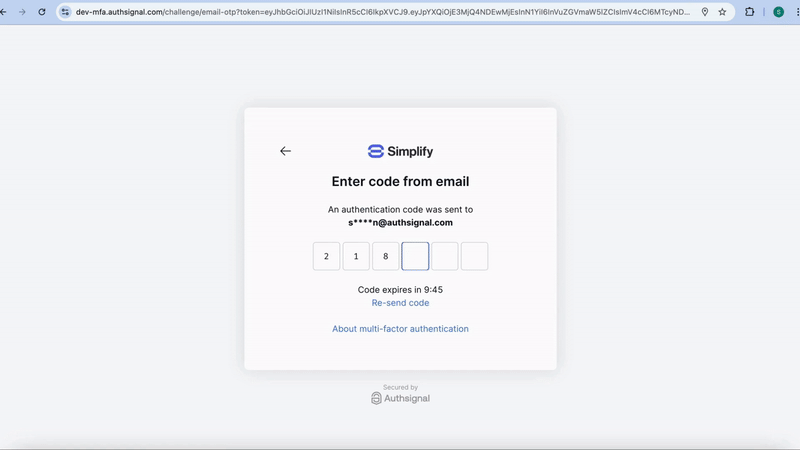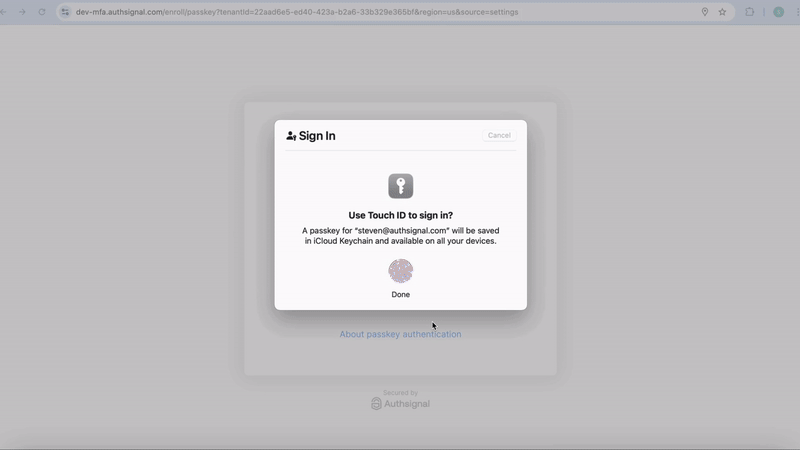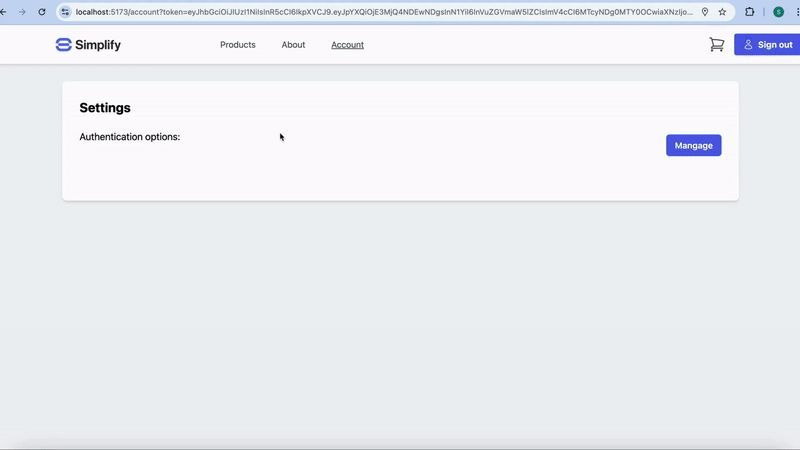
By default, the pre-built UI enforces strong binding automatically. Users must complete a challenge with an existing method before adding new ones. Implementation:- User clicks “Add authenticator” in your app
- Pre-built UI challenges with existing method (e.g., email OTP)
- After successful challenge, user can add new methods
- New authenticator is “bound” to the verified identity
Challenge-then-enroll flow ensures strong binding
Skipping the challenge
In some cases, you may want to skip the prerequisite challenge. This is appropriate when:- User just completed MFA in your app
- You’re in a trusted session context
- User is enrolling their first additional method immediately after signup
Use with extreme caution: Only skip the challenge when the user has been strongly authenticated within your current session. Misuse can create MFA bypass vulnerabilities.
Using Client SDKs
Client SDKs offer two approaches for maintaining strong binding:Option 1: Challenge-then-enroll
Present a challenge with an existing method, then allow enrollment:Option 2: Token-based binding
Generate a token on your backend (after strong authentication), then use it for enrollment: Backend: Generate bound tokenBackend security: Only generate tokens with
add:authenticators scope when the user has been strongly authenticated. This scope grants the ability to add new authenticators.
